Introduction & Overview
What is Throughput?
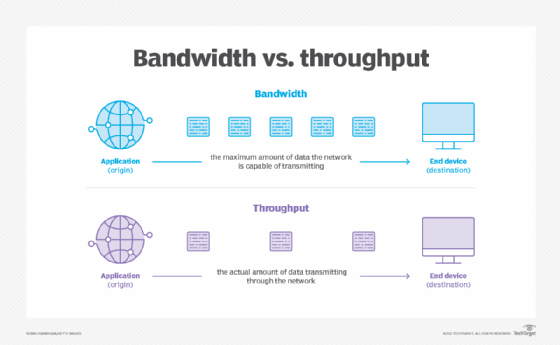
In the context of DevSecOps, throughput refers to the rate at which a system or process completes work—specifically, how many work units (such as code commits, builds, deployments, or test cases) are completed successfully within a defined time frame.
Throughput is a critical DevSecOps performance metric used to measure:
- Deployment efficiency
- Release velocity
- Security remediation speed
- Automated test coverage effectiveness
History or Background
Throughput has its roots in manufacturing and operations theory—especially in Lean and Agile methodologies. In software development, it’s been widely adopted via frameworks like:
- Agile/XP: Story points delivered per sprint
- DevOps: Deployments per day
- CI/CD pipelines: Successful builds/tests per hour
- DevSecOps: Security scans, patches, and fixes per pipeline cycle
With the rise of DevSecOps, throughput now encompasses not just functional delivery but secure delivery—measuring the secure features flowing through the SDLC.
Why is it Relevant in DevSecOps?
In DevSecOps, throughput is more than just speed. It is the balance between velocity and security. High throughput indicates a mature pipeline that delivers secure, tested, and compliant code efficiently.
Key reasons throughput matters:
- Tracks deployment frequency and security scan coverage
- Helps in identifying pipeline bottlenecks
- Indicates automation maturity
- Aligns with DORA metrics for high-performing teams
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Throughput | Number of completed and verified units of work (e.g., builds, deployments, patches) over time |
| Lead Time | Time between code commit and production release |
| Cycle Time | Time taken to complete one unit of work (e.g., one commit to deploy) |
| Pipeline Metrics | Includes throughput, mean time to recovery (MTTR), change failure rate, etc. |
| Security Throughput | Number of security-related tasks (e.g., scan reports, policy gates) processed in CI/CD |
How it Fits into the DevSecOps Lifecycle
Throughput touches multiple DevSecOps phases:
- Plan: Tracks delivery of secure stories
- Develop: Measures code and test commits
- Build/Test: Tracks automated test/security throughput
- Release: Monitors secure deployment frequency
- Operate/Monitor: Checks for compliance & anomaly response rate
Architecture & How It Works
Components and Internal Workflow
The throughput tracking workflow in DevSecOps typically includes:
- Source Code Commits: Tracked via Git, GitHub, GitLab
- CI/CD Jobs: Builds, tests, scans, and deployments
- Security Tool Integration: SAST, DAST, SCA outputs
- Monitoring & Analytics: Dashboards and alerts via tools like Prometheus, Datadog, Splunk
Sample Workflow Diagram (Text Description)
Dev Team → Git Commit → CI Pipeline Triggered →
→ Static Scan (SAST) → Build → Unit Tests →
→ DAST/SCA Scans → Artifact Creation →
→ Policy Gate Evaluation → Deployment to Staging →
→ Deployment to Production
→ Metrics Collection (Throughput, Scan Rate)
Integration Points with CI/CD or Cloud Tools
| Tool | Throughput Metric |
|---|---|
| Jenkins | Jobs/hour, test pass rate, scan success rate |
| GitHub Actions | Commits deployed, scan workflows completed |
| AWS CodePipeline | Artifacts deployed per region |
| Azure DevOps | Build and release rate |
| SonarQube | Code analysis frequency |
| OWASP ZAP/Burp | DAST scan frequency |
| Snyk/Checkmarx | Security issue resolution rate |
Installation & Getting Started
Basic Setup or Prerequisites
- CI/CD system (Jenkins, GitHub Actions, GitLab CI, etc.)
- Monitoring tool (Grafana, Datadog, Prometheus, ELK)
- Security tools (e.g., Snyk, SonarQube, OWASP ZAP)
- Metrics collector (custom scripts or built-in metrics plugins)
Hands-On: Step-by-Step Setup
🧪 Example: Tracking Throughput in GitHub Actions with Prometheus & Grafana
- Install Prometheus GitHub Exporter:
docker run -d -p 9100:9100 ghcr.io/prometheus/github-exporter
2. Configure GitHub Workflow to Push Metrics:
name: CI Pipeline
on: [push]
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v2
- name: Run Tests
run: npm test
- name: Push Throughput Metric
run: |
curl -X POST http://<prometheus_host>:9100/metrics \
-d 'ci_pipeline_throughput{job="build"} 1'
3. Visualize in Grafana:
- Add Prometheus as a data source.
- Create a dashboard with:
rate(ci_pipeline_throughput[1h])
4. Secure the metrics (optional):
- Integrate with OAuth
- Mask tokens via GitHub secrets
Real-World Use Cases
1. Security Patch Throughput in Banking
- Frequent deployment of security patches due to high regulatory pressure
- Measured by number of critical CVEs patched per sprint
2. DevSecOps in eCommerce
- Measuring secure feature delivery weekly
- Throughput = Number of successful builds + vulnerability scan passes
3. Automated Compliance in Healthcare
- Throughput of HIPAA-related code blocks and policy gates
- Automated audit trail of how many code units passed compliance gates
4. CI/CD Audit in FinTech
- Track throughput across environments (dev, stage, prod)
- Ensure no slowdown due to added security stages
Benefits & Limitations
Key Advantages
- Quantifies DevSecOps maturity
- Enables automated compliance audits
- Detects pipeline bottlenecks early
- Balances speed and security
- Promotes data-driven DevOps transformation
Common Challenges or Limitations
| Limitation | Mitigation |
|---|---|
| False sense of speed (ignoring quality) | Combine with DORA metrics |
| Complex to measure across tools | Use unified observability platforms |
| Misaligned team KPIs | Use throughput in conjunction with SLA/OKRs |
| Requires instrumentation | Start with open-source collectors |
Best Practices & Recommendations
🔐 Security Tips
- Include security throughput as a metric (scans, fixes, audits)
- Automate secure code checks in each PR
⚙ Performance & Maintenance
- Instrument throughput metrics at each CI/CD stage
- Set thresholds and alerts for anomalies
📜 Compliance Alignment
- Map throughput to regulatory goals (e.g., SOC 2 delivery SLA)
- Export logs and metrics for audits
🤖 Automation Ideas
- Auto-tag builds with throughput scores
- Pause pipeline if throughput drops below baseline
Comparison with Alternatives
| Metric | Use Case | Pros | Cons |
|---|---|---|---|
| Throughput | Speed + security | Comprehensive view | Needs instrumentation |
| Lead Time | Dev productivity | Simpler to calculate | Doesn’t include security |
| Change Failure Rate | Code quality | Security insight | Limited scope |
| MTTR | Ops recovery focus | Useful for downtime | Post-failure only |
✅ Use Throughput when you need to balance security, velocity, and delivery quality in CI/CD pipelines.
Conclusion
Throughput in DevSecOps is a powerful metric that aligns speed and security, reflecting the maturity of your delivery process. By tracking how fast secure, compliant, and tested changes flow through the system, teams can optimize both agility and risk posture.
Next Steps
- Start tracking throughput in one stage (e.g., SAST pass rate)
- Expand to end-to-end pipeline view
- Use dashboards to make data-driven security decisions