1. Introduction & Overview
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) is the practice of managing and provisioning computing infrastructure through machine-readable definition files, rather than through physical hardware configuration or interactive configuration tools. This includes automating servers, networks, databases, and application infrastructure setup using code.
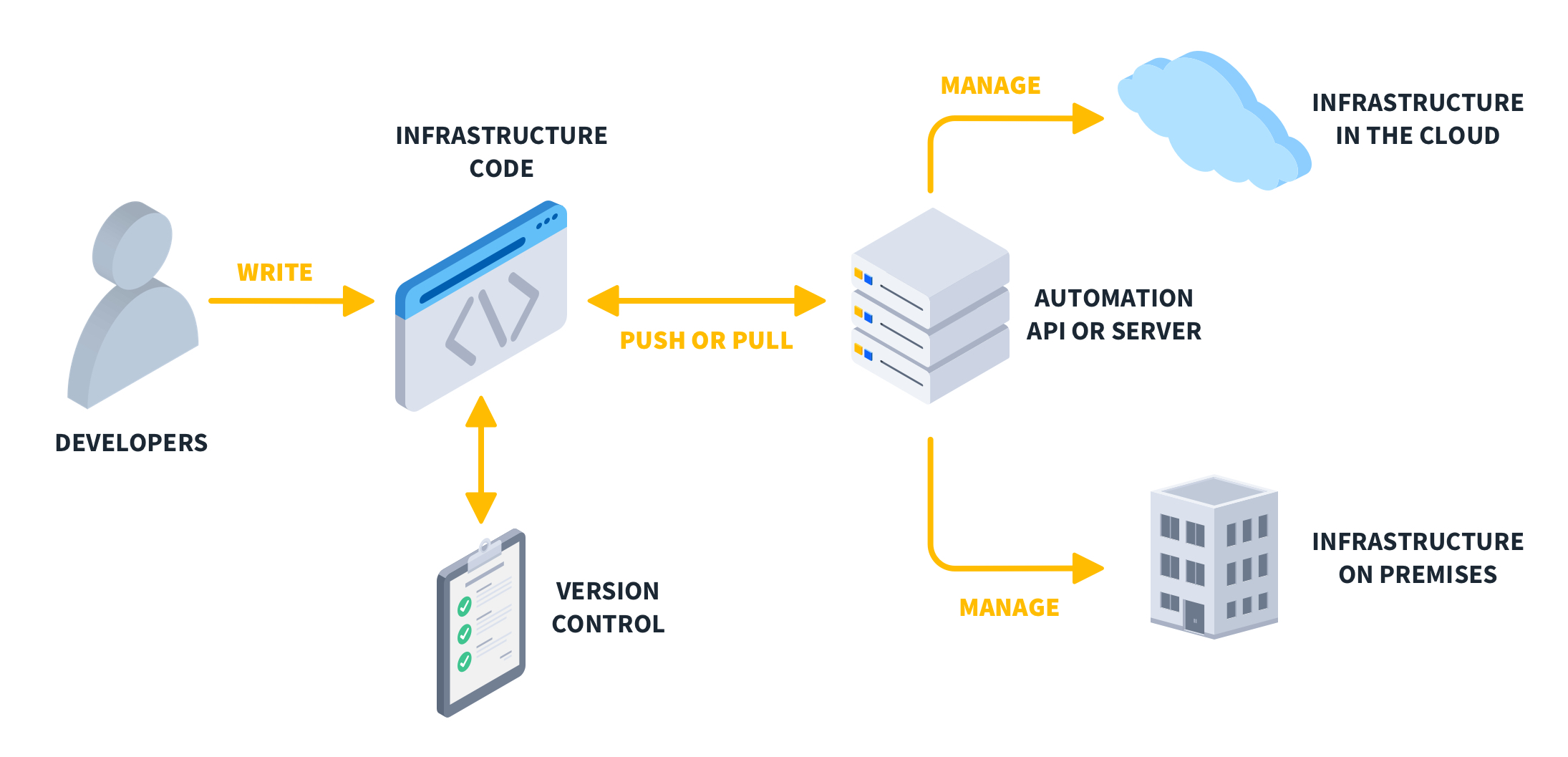
History and Background
- Early Days: Traditional infrastructure relied on manual provisioning using GUI tools or command-line interfaces.
- Rise of Automation: Configuration management tools like Puppet (2005), Chef (2009), and Ansible (2012) laid the foundation.
- Modern Era: Declarative tools like Terraform and CloudFormation elevated IaC by providing complete infrastructure orchestration.
Why IaC is Relevant in DevSecOps
- Speed & Efficiency: Rapid and repeatable infrastructure deployments.
- Security as Code: Embed security configurations and policies into code.
- Auditability: All changes are traceable through version control.
- Consistency: Eliminates drift between environments (dev, staging, production).
- Shift-Left Security: Apply security checks early in the CI/CD pipeline.
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Declarative IaC | Specifies what the desired state should be (e.g., Terraform, CloudFormation). |
| Imperative IaC | Specifies how to achieve the desired state step by step (e.g., Ansible). |
| Idempotency | Running the same code multiple times produces the same result. |
| Drift Detection | Identifying discrepancies between actual and expected infrastructure state. |
| Mutable vs Immutable | Mutable infrastructure is updated in place; immutable is replaced entirely. |
| Infrastructure Drift | When the live infrastructure differs from the defined IaC code. |
How IaC Fits into the DevSecOps Lifecycle
Plan → Code → Build → Test → Release → Deploy → Operate → Monitor → Secure
- Plan: Define infrastructure requirements as code.
- Build/Test: Validate IaC scripts and run security scans (e.g., tfsec, Checkov).
- Deploy: Use CI/CD pipelines to provision infrastructure.
- Operate/Secure: Continuously monitor compliance, enforce security baselines.
3. Architecture & How It Works
Components
- IaC Tools: Terraform, Ansible, CloudFormation, Pulumi.
- Version Control: GitHub, GitLab – stores the codebase and tracks changes.
- CI/CD Tools: Jenkins, GitHub Actions, GitLab CI – automate provisioning and testing.
- Cloud Providers: AWS, Azure, GCP – provide the resources to be managed.
- Security Scanners: tfsec, Checkov, Bridgecrew – audit infrastructure code.
Internal Workflow (Simplified)
- Developer writes infrastructure code.
- Code is pushed to version control.
- CI pipeline runs:
- Linting and formatting
- Static analysis for security
- Plan and apply changes
- Cloud provider provisions or updates infrastructure.
- Monitoring tools ensure drift detection and compliance.
Architecture Diagram (Text Description)

[ Developer ]
↓
[ Version Control (Git) ]
↓ Push
[ CI/CD Pipeline (e.g., GitHub Actions) ]
├──> Lint / Validate
├──> Security Scan (e.g., tfsec)
├──> terraform plan
└──> terraform apply
↓
[ Cloud Provider (AWS, GCP, Azure) ]
↓
[ Monitoring / Drift Detection / Logs ]
Integration Points
| Tool | Integration Use Case |
|---|---|
| Jenkins | Automate IaC deployments |
| GitHub Actions | Run Terraform plans and apply via workflows |
| tfsec/Checkov | Static security analysis of IaC scripts |
| AWS/GCP/Azure | Cloud-native provisioning |
4. Installation & Getting Started
Prerequisites
- Git installed
- Cloud provider account (e.g., AWS)
- Terraform installed (or preferred IaC tool)
- CLI credentials configured
Example: Deploying an AWS EC2 Instance with Terraform
# 1. Install Terraform
brew install terraform
# 2. Initialize a new Terraform project
mkdir my-iac-project && cd my-iac-project
terraform init
main.tf
provider "aws" {
region = "us-west-2"
}
resource "aws_instance" "example" {
ami = "ami-0abcdef1234567890"
instance_type = "t2.micro"
tags = {
Name = "DevSecOpsExample"
}
}
# 3. Initialize and apply
terraform init
terraform plan
terraform apply
5. Real-World Use Cases
Use Case 1: Automated Secure Cloud Environments
- Context: FinTech startup building a PCI-DSS compliant environment
- IaC Role: Automates VPCs, security groups, IAM roles
- Security Integration: Checkov integrated with CI for compliance checks
Use Case 2: Ephemeral Environments for Testing
- Context: Media company creates temporary testing environments
- IaC Role: Provision test infrastructure via GitHub Actions
- Security: Secrets managed via Vault + dynamic credentials
Use Case 3: Disaster Recovery Infrastructure
- Context: Healthcare firm needs reliable backup regions
- IaC Role: Use IaC to duplicate infrastructure across regions
- Security: Use signed commits and audit logs
Use Case 4: Continuous Compliance Auditing
- Context: Government SaaS provider
- IaC Role: Automate CIS/STIG baseline checks in every deploy
- Security: tfsec + policy-as-code using Open Policy Agent (OPA)
6. Benefits & Limitations
Key Advantages
- ✅ Version-controlled infrastructure
- ✅ Faster onboarding and reproducibility
- ✅ Easier rollback and disaster recovery
- ✅ Promotes collaboration between Dev, Sec, and Ops
Common Limitations
- ⚠️ Misconfiguration risk if not validated
- ⚠️ Steep learning curve for complex deployments
- ⚠️ Tool-specific limitations (e.g., CloudFormation is AWS-only)
- ⚠️ Secret sprawl if not integrated with secret managers
7. Best Practices & Recommendations
Security Tips
- Use policy-as-code (OPA, Sentinel) to enforce rules.
- Always run security scanners like tfsec, Checkov.
- Store secrets in vaults (HashiCorp Vault, AWS Secrets Manager).
- Use role-based access control (RBAC) for IaC execution.
Performance & Maintenance
- Modularize code using Terraform modules or Ansible roles.
- Use remote backends (e.g., S3 + DynamoDB) to store state.
- Keep IaC repositories separate from application code.
Compliance & Automation
- Integrate IaC checks into CI/CD.
- Automate drift detection with tools like Terraform Cloud or AWS Config.
- Use tagging standards for cost allocation and compliance visibility.
8. Comparison with Alternatives
| Approach | Description | Pros | Cons |
|---|---|---|---|
| Terraform (IaC) | Declarative, multi-cloud support | Cloud-agnostic, modular | Requires learning HCL |
| CloudFormation | AWS-specific IaC | Tight AWS integration | AWS-only, verbose syntax |
| Ansible | Imperative, great for config mgmt | SSH-based, easy syntax | Not ideal for provisioning infra |
| Scripts (Shell/Python) | Ad-hoc provisioning | Flexible | Hard to maintain, not scalable |
When to Choose IaC
- Multi-cloud or hybrid environments
- Need for infrastructure version control and compliance
- Security automation and drift detection are essential
9. Conclusion
Infrastructure as Code (IaC) is a foundational pillar of modern DevSecOps practices. It empowers teams to define infrastructure in a repeatable, secure, and auditable way. By integrating with security scanning tools, CI/CD systems, and cloud platforms, IaC allows organizations to shift security left while maintaining agility and speed.
Future Trends
- AI-assisted IaC for automated optimization
- GitOps and Policy-as-Code for infrastructure governance
- Self-healing infrastructure using event-driven automation
Next Steps
- Start small with a test project
- Integrate with CI/CD and security tools
- Join communities and stay updated