Introduction & Overview
Infrastructure as Code (IaC) is a transformative approach to managing and provisioning IT infrastructure through machine-readable configuration files, enabling automation, scalability, and reliability. In Site Reliability Engineering (SRE), IaC ensures consistent, repeatable, and efficient infrastructure management, aligning with SRE principles of reducing toil and improving system reliability.
This tutorial provides an in-depth exploration of IaC in the context of SRE, covering its concepts, architecture, setup, real-world applications, benefits, limitations, best practices, and comparisons with alternatives. It is designed for technical readers, including SREs, DevOps engineers, and cloud architects.
What is Infrastructure as Code (IaC)?
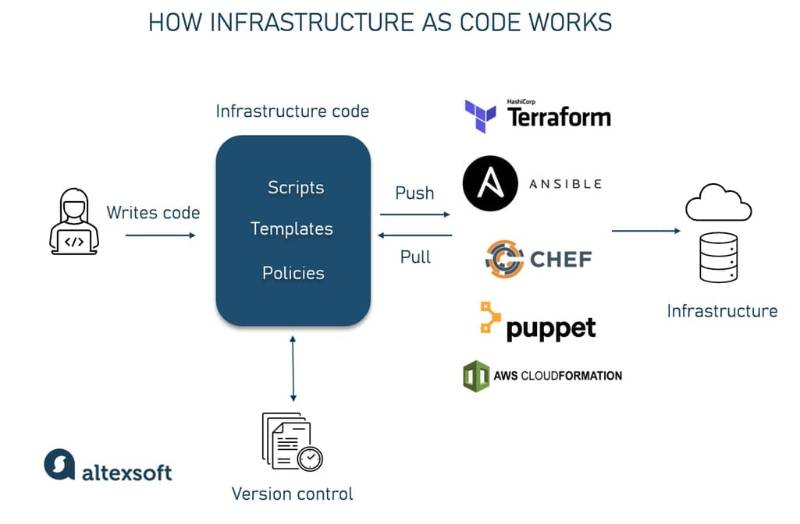
IaC refers to the practice of managing infrastructure (servers, networks, storage, etc.) using code and automation tools instead of manual processes. It treats infrastructure configurations as software, enabling version control, testing, and automation.
- Declarative IaC: Define the desired state (e.g., Terraform, AWS CloudFormation).
- Imperative IaC: Specify step-by-step instructions (e.g., Ansible, Chef).
History or Background
IaC emerged in the early 2000s with the rise of cloud computing and DevOps. Tools like Puppet (2005) and Chef (2009) laid the groundwork, followed by Terraform (2014) and AWS CloudFormation. The need for scalable, repeatable infrastructure in cloud environments drove IaC adoption, aligning with SRE’s focus on automation and reliability.
Why is it Relevant in Site Reliability Engineering?
SRE emphasizes reducing manual toil, ensuring system reliability, and enabling rapid recovery. IaC supports these goals by:
- Automation: Reduces human error and manual configuration.
- Consistency: Ensures identical environments across development, staging, and production.
- Scalability: Enables rapid provisioning of resources.
- Reliability: Facilitates disaster recovery through codified infrastructure.
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Infrastructure as Code (IaC) | Managing infrastructure using code, enabling automation and version control. |
| Declarative Approach | Specifies the desired state of infrastructure (e.g., Terraform). |
| Imperative Approach | Defines step-by-step instructions to achieve infrastructure state (e.g., Ansible). |
| State File | A file (e.g., Terraform’s terraform.tfstate) tracking the current state of infrastructure. |
| Idempotency | Ensuring repeated operations produce the same result without side effects. |
| Provider | A plugin or service (e.g., AWS, Azure) that IaC tools interact with to manage resources. |
How It Fits into the SRE Lifecycle
IaC integrates into the SRE lifecycle across:
- Design: Codifying infrastructure for consistent deployments.
- Deployment: Automating resource provisioning via CI/CD pipelines.
- Monitoring: Tracking infrastructure changes for reliability.
- Incident Response: Enabling rapid recovery by redeploying infrastructure from code.
- Postmortems: Version control helps analyze changes leading to incidents.
Architecture & How It Works
Components
- IaC Tool: Software like Terraform, Ansible, or CloudFormation that interprets code to provision resources.
- Configuration Files: Code defining infrastructure (e.g.,
.tffor Terraform,.ymlfor Ansible). - State Management: Tracks the current state (e.g., Terraform state file).
- Providers/Apis: Interface with cloud platforms (AWS, Azure, GCP).
- Version Control: Stores IaC code (e.g., Git).
Internal Workflow
- Write IaC code defining the desired infrastructure state.
- Store code in a version control system (e.g., Git).
- IaC tool reads the code and interacts with provider APIs.
- Provider provisions or updates resources to match the desired state.
- State file updates to reflect the current infrastructure.
Architecture Diagram Description
The architecture consists of:
- Developer/SRE: Writes IaC code.
- Version Control System (VCS): Stores IaC code (e.g., GitHub).
- IaC Tool: Processes code (e.g., Terraform).
- Cloud Provider APIs: Interface with AWS, Azure, etc.
- Infrastructure: Provisioned resources (servers, networks).
- CI/CD Pipeline: Automates IaC execution.
- State Storage: Stores state files (e.g., S3 bucket for Terraform).
Developer/SRE
|
v
[ Git Repository ]
|
v
[ CI/CD Pipeline ] ---> [ Testing & Linting ]
|
v
[ IaC Tool (Terraform/Ansible/Pulumi) ]
|
v
[ Cloud Provider APIs ]
|
v
[ Provisioned Infra (VMs, DBs, Networks, Load Balancers) ]
Diagram: Imagine a flowchart where the Developer pushes IaC code to a VCS, which triggers a CI/CD pipeline. The pipeline runs the IaC tool, which communicates with cloud provider APIs to provision resources. A state file is stored in a secure backend (e.g., S3) and updated after provisioning.
Integration Points with CI/CD or Cloud Tools
- CI/CD: Tools like Jenkins, GitHub Actions, or GitLab CI integrate IaC for automated deployments.
- Cloud Tools: IaC interacts with cloud-native tools (e.g., AWS CloudFormation, Azure Resource Manager).
- Monitoring: Tools like Prometheus or Datadog monitor IaC-provisioned resources.
Installation & Getting Started
Basic Setup or Prerequisites
- System Requirements: Linux, macOS, or Windows with a command-line interface.
- Software: Install an IaC tool (e.g., Terraform, Ansible).
- Cloud Account: AWS, Azure, or GCP account with API access.
- Version Control: Git installed and configured.
- Text Editor: VS Code or any editor for writing IaC code.
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
This guide uses Terraform to provision an AWS EC2 instance.
- Install Terraform:
- Download Terraform from
https://www.terraform.io/downloads.html. - Unzip and move to
/usr/local/bin(Linux/macOS) or add to PATH (Windows). - Verify:
terraform --version.
- Download Terraform from
- Set Up AWS Credentials:
- Create an AWS IAM user with
AmazonEC2FullAccess. - Configure credentials:
- Create an AWS IAM user with
aws configure
# Enter Access Key ID, Secret Access Key, region (e.g., us-east-1)3. Write Terraform Code:
- Create a file
main.tf:
provider "aws" {
region = "us-east-1"
}
resource "aws_instance" "example" {
ami = "ami-0c55b159cbfafe1f0" # Amazon Linux 2 AMI
instance_type = "t2.micro"
}4. Initialize Terraform:
terraform init5. Plan and Apply:
terraform plan
terraform apply6. Verify: Check the AWS console for the EC2 instance.
7. Clean Up:
terraform destroyReal-World Use Cases
Scenario 1: Autoscaling Web Application
An SRE team uses Terraform to provision an autoscaling group in AWS, ensuring the application scales based on demand. IaC defines load balancers, EC2 instances, and scaling policies.
Scenario 2: Disaster Recovery
A financial company uses IaC to replicate infrastructure across regions. If a primary region fails, Terraform redeploys the infrastructure in a secondary region, minimizing downtime.
Scenario 3: CI/CD Pipeline Integration
An e-commerce platform uses Ansible with GitHub Actions to deploy infrastructure changes alongside application code, ensuring consistent environments.
Industry-Specific Example: Healthcare
A healthcare provider uses IaC to manage HIPAA-compliant infrastructure, automating the provisioning of secure VPCs, encrypted databases, and audit logs.
Benefits & Limitations
Key Advantages
- Consistency: Identical environments across development, staging, and production.
- Automation: Reduces manual configuration, aligning with SRE’s toil reduction.
- Version Control: Tracks infrastructure changes, aiding audits and rollbacks.
- Scalability: Simplifies provisioning of large-scale infrastructure.
Common Challenges or Limitations
- Learning Curve: Requires understanding of both IaC tools and cloud platforms.
- State Management: Improper handling of state files can lead to inconsistencies.
- Drift: Infrastructure may diverge from code due to manual changes.
- Security Risks: Hard-coded secrets in IaC code can lead to vulnerabilities.
Best Practices & Recommendations
Security Tips
- Store secrets in secure vaults (e.g., AWS Secrets Manager, HashiCorp Vault).
- Use least privilege principles for IAM roles.
- Encrypt state files and store them in secure backends (e.g., S3 with encryption).
Performance
- Modularize IaC code for reusability (e.g., Terraform modules).
- Use parallel execution for large deployments (e.g.,
terraform apply -parallelism=10).
Maintenance
- Regularly update IaC tools and providers.
- Monitor infrastructure drift using tools like
terraform planor Driftctl.
Compliance Alignment
- Use IaC to enforce compliance (e.g., CIS benchmarks, HIPAA).
- Implement policy-as-code with tools like Open Policy Agent (OPA).
Automation Ideas
- Integrate IaC with CI/CD for automated deployments.
- Use GitOps to manage infrastructure changes via pull requests.
Comparison with Alternatives
| Feature/Tool | Terraform (IaC) | Manual Configuration | Configuration Management (Ansible/Chef) |
|---|---|---|---|
| Approach | Declarative | Manual | Imperative/Declarative |
| Scalability | High | Low | Medium |
| Version Control | Yes | No | Yes |
| Cloud Support | Multi-cloud | Platform-specific | Multi-cloud |
| Use Case | Infrastructure provisioning | Small-scale setups | Server configuration |
When to Choose IaC
- Choose IaC for large-scale, cloud-native, or multi-cloud environments.
- Opt for configuration management tools like Ansible for server-level configurations.
- Avoid manual configuration for production systems due to error-proneness.
Conclusion
IaC is a cornerstone of modern SRE, enabling automation, consistency, and reliability in infrastructure management. By codifying infrastructure, SREs can reduce toil, improve scalability, and ensure rapid recovery. As cloud adoption grows, IaC will evolve with trends like GitOps and policy-as-code.
Next Steps
- Explore advanced IaC tools like Pulumi or Crossplane.
- Join communities like HashiCorp’s Terraform Community or AWS DevOps forums.
- Official Docs: Terraform, Ansible, AWS CloudFormation.