Introduction & Overview
GitOps is a transformative operational framework that leverages Git as the single source of truth for managing infrastructure and application deployments, aligning closely with Site Reliability Engineering (SRE) principles. By combining DevOps practices like version control, collaboration, and CI/CD with infrastructure automation, GitOps ensures consistent, reliable, and automated management of cloud-native systems. This tutorial provides a detailed guide on GitOps in the context of SRE, covering its concepts, architecture, setup, use cases, benefits, limitations, best practices, and comparisons with alternatives.
What is GitOps?
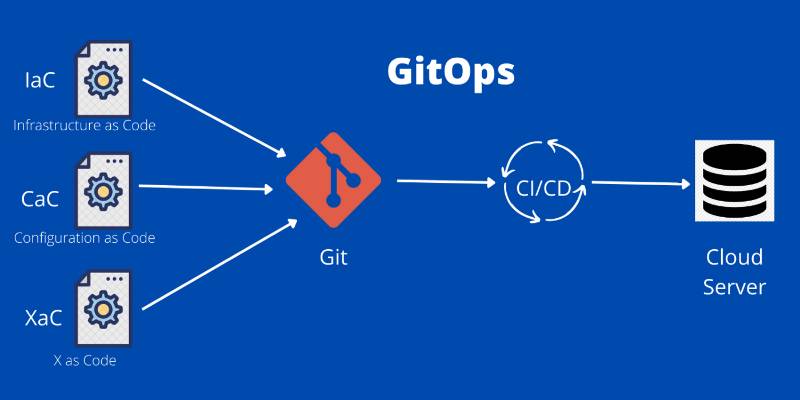
GitOps is an operational model that uses Git repositories to store declarative infrastructure and application configurations, automating their deployment through continuous delivery pipelines. Changes are proposed via pull requests (PRs), reviewed, and applied automatically to ensure the infrastructure matches the desired state defined in Git. This approach enhances collaboration, traceability, and reliability, making it a cornerstone for modern SRE practices.
In short:
👉 Git = Source of Truth
👉 Automation = Enforces Desired State
👉 Observability = Ensures Reliability
History or Background
GitOps was coined by Weaveworks in 2017, building on the principles of Infrastructure as Code (IaC) and DevOps. It emerged as a response to the complexities of managing cloud-native environments, particularly Kubernetes-based systems. By leveraging Git’s version control capabilities, GitOps introduced a declarative, auditable, and automated approach to infrastructure management. Its adoption has grown with the rise of Kubernetes, tools like ArgoCD and Flux, and the need for scalable, reliable deployment workflows.
- Introduced by Weaveworks in 2017 to streamline Kubernetes operations.
- Inspired by DevOps & Infrastructure as Code (IaC) principles.
- Grew popular with cloud-native adoption and tools like ArgoCD, FluxCD, Jenkins X.
- Now widely adopted in SRE practices for reliability, compliance, and automation.
Why is it Relevant in Site Reliability Engineering?
SRE focuses on maintaining reliable, scalable systems while balancing operational efficiency and innovation. GitOps aligns with SRE by:
- Automating Infrastructure Management: Reduces manual interventions, minimizing errors and toil.
- Enhancing Reliability: Ensures infrastructure consistency through declarative configurations and automated reconciliation.
- Supporting Scalability: Simplifies management of complex, multi-cluster environments.
- Improving Observability: Provides audit trails via Git history, aiding incident analysis and compliance.
- Fostering Collaboration: Enables developers and SREs to work together via familiar Git workflows.
Core Concepts & Terminology
Key Terms and Definitions
- Infrastructure as Code (IaC): The practice of defining infrastructure configurations as code, stored in version-controlled repositories.
- Git Repository: The single source of truth storing declarative configurations for infrastructure and applications.
- Declarative Configuration: Defining the desired state of a system (e.g., Kubernetes manifests) rather than imperative instructions.
- Reconciliation Loop: A process where a GitOps tool continuously monitors and aligns the actual infrastructure state with the desired state in Git.
- Pull Request (PR)/Merge Request (MR): A Git mechanism for proposing, reviewing, and approving infrastructure changes.
- GitOps Operator: Tools like ArgoCD or Flux that automate deployment and ensure state consistency.
- Configuration Drift: When the actual infrastructure state deviates from the desired state in Git.
| Term | Description |
|---|---|
| Desired State | The system configuration declared in Git repositories (YAML, Helm, Terraform, etc.). |
| Observed State | The actual, real-time state of the system in production. |
| Reconciliation Loop | Continuous automation that aligns observed state with desired state. |
| Pull Model | GitOps agents (ArgoCD/Flux) pull changes from Git and apply them. |
| Single Source of Truth | Git acts as the only authority for infra & app definitions. |
How It Fits into the Site Reliability Engineering Lifecycle
GitOps integrates seamlessly into the SRE lifecycle, which includes designing, deploying, monitoring, and improving systems:
- Design & Planning: SREs define infrastructure requirements as code in Git, ensuring reproducibility.
- Deployment: Automated CI/CD pipelines apply changes from Git, reducing manual toil.
- Monitoring & Observability: GitOps tools detect configuration drift, supporting SLO-driven reliability.
- Incident Response: Git history enables quick rollbacks and root cause analysis.
- Continuous Improvement: Encourages experimentation with version-controlled changes, aligning with SRE’s focus on iterative enhancements.
| SRE Activity | GitOps Role |
|---|---|
| Change Management | All changes tracked via Git commits & PRs. |
| Incident Response | Rollback to stable Git state. |
| Capacity Planning | Declarative infra scaling via Git manifests. |
| Error Budgets | Automates releases while respecting SLOs. |
| Monitoring | Integrates with observability tools for state drift detection. |
Architecture & How It Works
Components
A GitOps architecture typically includes:
- Git Repository: Stores declarative configurations (e.g., YAML files for Kubernetes, Terraform scripts).
- CI/CD Pipeline: Automates building, testing, and pushing changes to the Git repository.
- GitOps Operator: Monitors the repository and applies changes to the infrastructure (e.g., ArgoCD, Flux).
- Container Platform: Often Kubernetes, where applications and infrastructure are deployed.
- Monitoring Tools: Track system health and detect configuration drift (e.g., Prometheus, Grafana).
Internal Workflow
- Define Desired State: Engineers commit infrastructure configurations to a Git repository.
- Pull Request Process: Changes are proposed via PRs, reviewed, and merged after approval.
- CI Pipeline: Validates changes through automated tests (e.g., linting, compliance checks).
- GitOps Operator: Detects changes in the repository via polling or webhooks and applies them to the infrastructure.
- Reconciliation Loop: Continuously monitors the infrastructure to ensure it matches the Git-defined state, correcting any drift.
- Observability: Logs and metrics provide visibility into deployments and system health.
Architecture Diagram
Below is a textual description of a GitOps architecture diagram, as images cannot be generated:
[Developer] --> [Git Repository (GitHub/GitLab)]
| |
| v
| [CI Pipeline (GitHub Actions/Jenkins)]
| |
| v
| [GitOps Operator (ArgoCD/Flux)]
| |
| v
| [Kubernetes Cluster]
| |
| v
| [Monitoring (Prometheus/Grafana)]
v
[Feedback Loop: Logs, Metrics, Alerts]
- Developer: Commits changes to the Git repository.
- Git Repository: Stores infrastructure and application configurations.
- CI Pipeline: Validates and tests changes before merging.
- GitOps Operator: Synchronizes the cluster with the repository’s desired state.
- Kubernetes Cluster: Hosts applications and infrastructure.
- Monitoring: Provides observability and alerts for drift or issues.
Integration Points with CI/CD or Cloud Tools
- CI/CD Tools: GitHub Actions, Jenkins, or GitLab CI validate and trigger deployments.
- Cloud Platforms: AWS, GCP, Azure integrate via IaC tools like Terraform or CloudFormation.
- Container Orchestration: Kubernetes is the primary platform, with tools like Helm for templating.
- Monitoring & Logging: Prometheus, Grafana, and ELK stack provide observability.
- Secret Management: HashiCorp Vault or AWS Secrets Manager for secure credential handling.
Installation & Getting Started
Basic Setup or Prerequisites
- Git Repository: A Git hosting service (e.g., GitHub, GitLab, Bitbucket).
- Kubernetes Cluster: A running cluster (e.g., Minikube for local testing, EKS/GKE for production).
- GitOps Tool: ArgoCD or Flux installed on the cluster.
- CI/CD Tool: GitHub Actions, Jenkins, or equivalent for automated testing.
- kubectl: Kubernetes command-line tool for cluster interaction.
- Basic Knowledge: Familiarity with Git, YAML, and Kubernetes.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
This guide sets up a basic GitOps workflow using ArgoCD on a Kubernetes cluster.
- Set Up a Kubernetes Cluster:
- For local testing, install Minikube:
minikube startVerify the cluster:
kubectl get nodes2. Install ArgoCD:
- Apply the ArgoCD manifests:
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml- Access the ArgoCD UI:
kubectl port-forward svc/argocd-server -n argocd 8080:443- Log in using the default admin password (retrieve it using
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d).
3. Create a Git Repository:
- Initialize a repository on GitHub/GitLab with a sample Kubernetes manifest:
# nginx-deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:latest
ports:
- containerPort: 80- Push the file to the repository.
4. Configure ArgoCD:
- Create an ArgoCD application:
# application.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: nginx-app
namespace: argocd
spec:
project: default
source:
repoURL: <your-git-repo-url>
targetRevision: main
path: .
destination:
server: https://kubernetes.default.svc
namespace: default
syncPolicy:
automated:
prune: true
selfHeal: true- Apply the application:
kubectl apply -f application.yaml
5. Verify Deployment:
- Check the application status in the ArgoCD UI or via CLI:
argocd app get nginx-app- Verify the Nginx deployment:
kubectl get pods6. Update Infrastructure:
- Update
nginx-deployment.yaml(e.g., change replicas to 3), commit, and push to Git. - ArgoCD will detect the change and update the cluster automatically.
Real-World Use Cases
- Managing Multi-Cluster Kubernetes Deployments:
- Scenario: A financial services company manages multiple Kubernetes clusters across regions for high availability.
- GitOps Application: ArgoCD synchronizes configurations across clusters from a single Git repository, ensuring consistency. SREs use PRs to update configurations, with automated compliance checks.
- Outcome: Reduced configuration drift, faster deployments, and improved reliability for critical financial applications.
- Automating Blue/Green Deployments:
- Scenario: An e-commerce platform needs zero-downtime deployments for its microservices.
- GitOps Application: Flux manages blue/green deployments by updating Kubernetes manifests in Git. The operator applies changes and monitors health before switching traffic.
- Outcome: Seamless rollouts, reduced risk, and improved customer experience during updates.
- Disaster Recovery:
- Scenario: A healthcare provider requires rapid recovery from infrastructure failures.
- GitOps Application: GitOps enables quick rollbacks by reverting to a previous Git commit. SREs use Git history to identify and restore stable configurations.
- Outcome: Minimized downtime and ensured compliance with healthcare regulations.
- Multi-Environment Management:
- Scenario: A gaming company manages development, staging, and production environments.
- GitOps Application: Separate Git branches (e.g.,
dev,staging,prod) store environment-specific configurations. ArgoCD deploys changes to the respective environments. - Outcome: Streamlined environment management, reduced errors, and faster iteration cycles.
Benefits & Limitations
Key Advantages
- Automation: Eliminates manual configuration, reducing toil and errors.
- Traceability: Git provides a full audit trail for changes, aiding compliance.
- Reliability: Reconciliation loops ensure infrastructure matches the desired state.
- Collaboration: PRs enable developer-SRE collaboration via familiar workflows.
- Scalability: Simplifies management of complex, multi-cluster environments.
Common Challenges or Limitations
- Learning Curve: Teams new to Git or Kubernetes may face initial complexity.
- Tooling Dependency: Relies on tools like ArgoCD or Flux, which require setup and maintenance.
- Security Risks: Misconfigured repositories or credentials can expose sensitive data.
- Not Universal: Primarily designed for Kubernetes; adapting to other systems (e.g., VMs) requires additional plugins.
Best Practices & Recommendations
Security Tips
- Restrict Repository Access: Use role-based access control (RBAC) to limit who can push to the main branch.
- Encrypt Secrets: Use tools like HashiCorp Vault or Sealed Secrets to manage sensitive data.
- Audit Logs: Regularly review Git history for unauthorized changes.
Performance
- Optimize Reconciliation: Configure polling intervals or webhooks to balance performance and responsiveness.
- Minimize Drift: Regularly validate configurations to prevent drift accumulation.
Maintenance
- Version Control Best Practices: Use clear commit messages and structured PRs for clarity.
- Automate Testing: Integrate linting and compliance checks in the CI pipeline.
Compliance Alignment
- Policy as Code: Define compliance rules in Git (e.g., OPA policies) to enforce standards.
- Audit Trails: Leverage Git logs for regulatory reporting.
Automation Ideas
- Automated Rollbacks: Configure operators to revert to stable states on failure.
- Dynamic Environments: Create temporary environments for PRs using tools like Kustomize.
Comparison with Alternatives
| Aspect | GitOps | Traditional DevOps | Ansible/Puppet | Terraform |
|---|---|---|---|---|
| Approach | Declarative, Git-based | Imperative or declarative | Imperative scripting | Declarative IaC |
| Source of Truth | Git repository | Various (scripts, configs) | Playbooks/Recipes | State files |
| Automation | Continuous reconciliation | Manual or pipeline-driven | Script-driven | Plan/apply cycles |
| Scalability | High (Kubernetes-focused) | Moderate | Moderate | High |
| Collaboration | PR-based, collaborative | Limited by tooling | Limited | PR-based |
| Use Case | Cloud-native, Kubernetes | Broad, legacy systems | Config management | Multi-cloud IaC |
When to Choose GitOps
- Choose GitOps: For Kubernetes-based, cloud-native environments requiring high automation, collaboration, and reliability.
- Choose Alternatives:
- Traditional DevOps: For legacy systems or non-Git workflows.
- Ansible/Puppet: For configuration management of non-containerized systems.
- Terraform: For multi-cloud infrastructure provisioning without continuous reconciliation.
Conclusion
GitOps revolutionizes infrastructure management in SRE by providing a declarative, Git-centric approach to automation, reliability, and collaboration. Its integration with Kubernetes, CI/CD pipelines, and monitoring tools makes it ideal for modern cloud-native environments. While it has a learning curve and tooling dependencies, its benefits in scalability, traceability, and reduced toil make it a powerful choice for SRE teams.
Future Trends
- Serverless and Edge Computing: GitOps is expanding to manage serverless and edge architectures.
- Policy as Code: Enhanced integration with tools like OPA for compliance.
- AI-Driven Operations: Machine learning for automated failure detection and rollbacks.
Next Steps
- Experiment with ArgoCD or Flux on a local Kubernetes cluster.
- Explore advanced features like Kustomize or Helm for configuration management.
- Join the GitOps community for best practices and updates.
Resources
- Official ArgoCD Documentation: https://argo-cd.readthedocs.io/
- Flux Documentation: https://fluxcd.io/
- Weaveworks GitOps Guide: https://www.weave.works/docs/
- CNCF GitOps Working Group: https://github.com/cncf/tag-app-delivery