Introduction & Overview
Blue-Green Deployment is a release management strategy that minimizes downtime and risk by running two identical production environments, referred to as “Blue” and “Green.” This approach is pivotal in Site Reliability Engineering (SRE) for ensuring high availability, seamless updates, and robust system reliability.
What is Blue-Green Deployment?
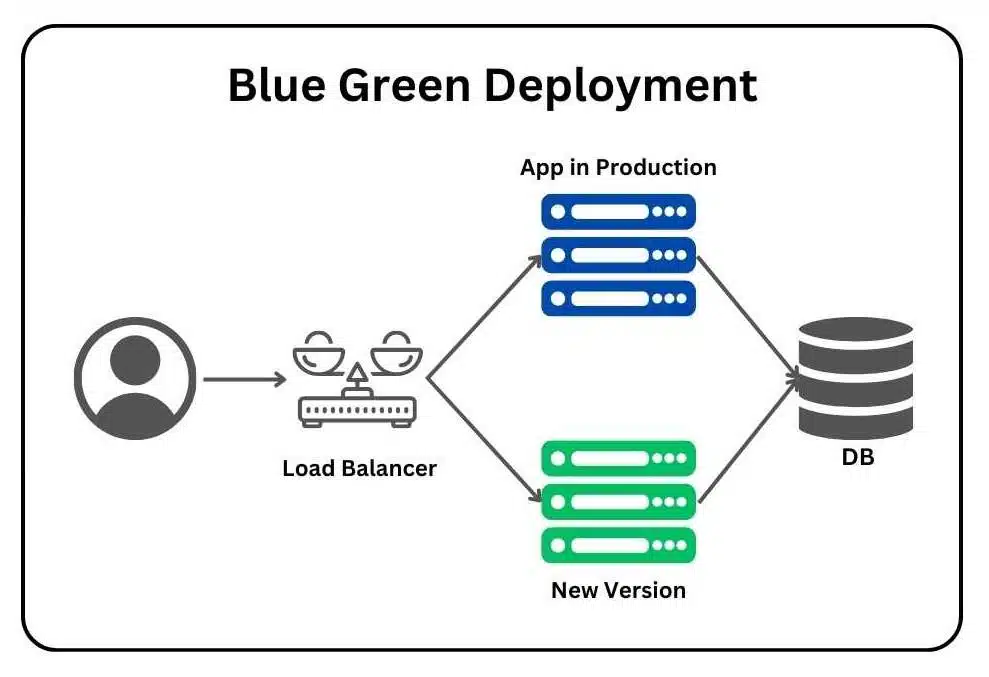
Blue-Green Deployment involves maintaining two production-ready environments:
- Blue Environment: The current live environment serving user traffic.
- Green Environment: The new environment with the updated application version, ready to take over once validated.
The process involves deploying the new version to the Green environment, testing it thoroughly, and then switching traffic from Blue to Green. If issues arise, traffic can revert to the Blue environment, ensuring zero downtime.
History or Background
The Blue-Green Deployment strategy emerged in the early 2000s as organizations sought to reduce downtime during software releases. It gained prominence with the rise of DevOps and SRE practices, where continuous delivery and high availability became critical. The term was popularized by Martin Fowler in his 2010 blog post and the book Continuous Delivery by Jez Humble and David Farley. It has since become a cornerstone of modern deployment practices, especially in cloud-native and microservices architectures.
- First described in continuous delivery practices (2005–2010).
- Popularized by Martin Fowler and Jez Humble in the book Continuous Delivery (2010).
- Widely adopted by cloud-native SRE teams at Netflix, Amazon, Google, etc.
Why is it Relevant in Site Reliability Engineering?
In SRE, Blue-Green Deployment aligns with the principles of reliability, automation, and scalability:
- Minimized Downtime: Switching between environments ensures uninterrupted service.
- Risk Mitigation: The ability to roll back to the stable Blue environment reduces deployment risks.
- Scalability: Supports rapid iteration and scaling in cloud environments.
- Automation: Integrates seamlessly with CI/CD pipelines, a key focus in SRE for reducing toil.
This approach is particularly valuable in industries like finance, e-commerce, and healthcare, where downtime can lead to significant financial or operational losses.
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Blue Environment | The live production environment currently handling user traffic. |
| Green Environment | The staging environment with the new version, ready for testing and switch. |
| Traffic Switch | The process of redirecting user traffic from Blue to Green after validation. |
| Rollback | Reverting traffic to the Blue environment if the Green environment fails. |
| Canary Release | A related strategy where a small subset of traffic is routed to the new version for testing. |
How It Fits into the Site Reliability Engineering Lifecycle
Blue-Green Deployment integrates into the SRE lifecycle as follows:
- Design & Development: Ensures environments are architected for redundancy and scalability.
- Deployment: Facilitates safe and automated rollouts with minimal user impact.
- Monitoring & Incident Response: Supports post-deployment validation and quick rollback if issues are detected.
- Post-Mortem & Learning: Provides insights into deployment failures, improving future iterations.
Architecture & How It Works
Components and Internal Workflow
Blue-Green Deployment relies on the following components:
- Application Servers: Identical sets of servers for Blue and Green environments.
- Load Balancer: Routes traffic between Blue and Green environments.
- Database: A shared or synchronized database to ensure data consistency across environments.
- CI/CD Pipeline: Automates the deployment of new code to the Green environment.
- Monitoring Tools: Validates the Green environment’s health before and after the traffic switch.
Workflow:
- Deploy the new application version to the Green environment.
- Run automated tests (unit, integration, smoke) in Green.
- Validate Green’s performance using monitoring tools (e.g., Prometheus, Grafana).
- Switch the load balancer to route traffic to Green.
- Monitor Green for issues; if stable, decommission Blue or keep it for rollback.
- If issues arise, revert traffic to Blue and troubleshoot Green.
Architecture Diagram
Below is a textual representation of the Blue-Green Deployment architecture:
+-------------------+ +-------------------+
| Blue Env | | Green Env |
| (Live) | | (New Version) |
| App Servers | | App Servers |
| Version X | | Version X+1 |
+-------------------+ +-------------------+
| |
| |
v v
+-------------------+ +-------------------+
| Database |<----->| Database |
| (Shared/Synced) | | (Shared/Synced) |
+-------------------+ +-------------------+
^
|
v
+-------------------+
| Load Balancer |
| (Routes Traffic)|
+-------------------+
^
|
v
+-------------------+
| End Users |
+-------------------+
Description: The load balancer directs traffic to either the Blue or Green environment. Both environments connect to a shared or synchronized database to ensure data consistency. Monitoring tools observe both environments, and the CI/CD pipeline deploys updates to the Green environment.
Integration Points with CI/CD or Cloud Tools
- CI/CD Tools: Jenkins, GitLab CI, or CircleCI automate deployments to the Green environment and trigger tests.
- Cloud Platforms: AWS Elastic Load Balancer, Azure Traffic Manager, or Google Cloud Load Balancing handle traffic switching.
- Container Orchestration: Kubernetes or Docker Swarm manage Blue and Green environments as separate clusters or namespaces.
- Monitoring: Tools like Datadog, New Relic, or Prometheus ensure the Green environment is stable before switching.
Installation & Getting Started
Basic Setup or Prerequisites
To implement Blue-Green Deployment, you need:
- Infrastructure: Two identical environments (Blue and Green) with application servers, load balancers, and databases.
- CI/CD Pipeline: Tools like Jenkins, GitHub Actions, or GitLab CI for automation.
- Cloud Provider: AWS, Azure, GCP, or on-premises infrastructure with load balancing capabilities.
- Monitoring Tools: Prometheus, Grafana, or ELK Stack for health checks.
- Configuration Management: Terraform, Ansible, or CloudFormation for environment setup.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
This guide demonstrates a Blue-Green Deployment using AWS Elastic Load Balancer (ELB) and EC2 instances.
- Set Up Two EC2 Environments:
- Launch two sets of EC2 instances (e.g., Blue and Green) with the same application stack.
- Example: Use an AMI with your application (e.g., Node.js app).
- Tag instances as
BlueandGreenfor identification.
- Configure a Load Balancer:
- Create an Application Load Balancer (ALB) in AWS.
- Set up two target groups:
Blue-TargetandGreen-Target. - Register Blue instances to
Blue-Targetand Green instances toGreen-Target.
- Set Up a Shared Database:
- Use Amazon RDS with read replicas or a synchronized database to ensure data consistency.
- Configure both environments to connect to the same RDS instance.
- Deploy Application to Green:
# SSH into Green instances
ssh -i key.pem ec2-user@<green-instance-ip>
# Pull and deploy new version
git pull origin main
npm install
pm2 restart app5. Run Automated Tests:
# Example: Run tests using a CI/CD pipeline (e.g., GitHub Actions)
npm test6. Switch Traffic to Green:
- Update the ALB listener to route traffic to
Green-Target. - AWS CLI command:
aws elbv2 modify-listener --listener-arn <listener-arn> --default-actions Type=forward,TargetGroupArn=<green-target-arn>7. Monitor and Validate:
- Use CloudWatch or Prometheus to monitor Green’s performance (e.g., latency, error rates).
- If issues occur, revert traffic to
Blue-Targetusing a similar CLI command.
8. Decommission Blue:
- Once Green is stable, terminate or repurpose Blue instances.
Real-World Use Cases
Scenario 1: E-Commerce Platform
An e-commerce company uses Blue-Green Deployment to roll out a new checkout feature:
- Blue: Current version with stable checkout.
- Green: New version with an updated payment gateway.
- Process: Deploy to Green, test with synthetic transactions, switch traffic, and monitor for cart abandonment rates.
- Outcome: Zero downtime during peak shopping hours, with rollback capability if the new gateway fails.
Scenario 2: Financial Services
A banking application upgrades its transaction processing system:
- Blue: Existing system handling live transactions.
- Green: Updated system with improved fraud detection.
- Process: Green is tested with mock transactions, then switched during a low-traffic window.
- Outcome: Ensures regulatory compliance and uninterrupted service for customers.
Scenario 3: Healthcare Platform
A telemedicine platform deploys a new video consultation feature:
- Blue: Stable version for patient consultations.
- Green: New version with enhanced video streaming.
- Process: Green undergoes load testing, followed by a traffic switch.
- Outcome: Maintains HIPAA compliance with seamless user experience.
Scenario 4: SaaS Application
A SaaS provider updates its API backend:
- Blue: Current API version.
- Green: New API with performance optimizations.
- Process: Green is validated with API tests, then traffic is switched.
- Outcome: Reduces latency for clients with minimal disruption.
Benefits & Limitations
Key Advantages
| Benefit | Description |
|---|---|
| Zero Downtime | Traffic switching ensures continuous availability. |
| Easy Rollback | Revert to Blue environment if Green fails, reducing risk. |
| Testing in Production | Green environment allows real-world testing without affecting users. |
| Scalability | Supports cloud-native architectures and rapid iteration. |
Common Challenges or Limitations
| Limitation | Description |
|---|---|
| Resource Cost | Maintaining two environments doubles infrastructure costs. |
| Database Synchronization | Shared databases require careful schema management to avoid conflicts. |
| Complexity | Requires robust CI/CD and monitoring to manage effectively. |
| Testing Overhead | Comprehensive testing in Green can delay deployments. |
Best Practices & Recommendations
Security Tips
- Isolate Environments: Use VPCs or network policies to secure Blue and Green environments.
- Access Control: Restrict access to Green until validated using IAM roles or similar mechanisms.
- Data Encryption: Ensure data in transit and at rest is encrypted, especially for shared databases.
Performance
- Load Testing: Simulate production traffic in Green to validate performance.
- Caching: Use Redis or Memcached to reduce database load during switches.
- Monitoring: Implement real-time monitoring with tools like Prometheus to detect issues early.
Maintenance
- Automation: Automate deployment, testing, and traffic switching with CI/CD pipelines.
- Version Control: Maintain separate configuration files for Blue and Green environments.
- Cleanup: Decommission or repurpose the old environment to optimize costs.
Compliance Alignment
- Audit Logs: Maintain logs of deployment and traffic switches for compliance (e.g., SOC 2, HIPAA).
- Data Consistency: Ensure database migrations are backward-compatible to support rollbacks.
Automation Ideas
- Use Terraform to provision Blue and Green environments.
- Implement GitOps with ArgoCD for automated deployments.
- Set up automated rollback triggers based on monitoring thresholds.
Comparison with Alternatives
| Feature | Blue-Green Deployment | Canary Release | Rolling Update |
|---|---|---|---|
| Downtime | None | Minimal | Possible |
| Rollback | Instant (switch back) | Gradual | Complex |
| Resource Usage | High (2 environments) | Moderate | Low |
| Testing | Full environment | Partial traffic | Incremental |
| Complexity | Moderate | High | Low |
When to Choose Blue-Green Deployment
- High Availability Needs: Ideal for applications requiring zero downtime (e.g., e-commerce, banking).
- Critical Updates: Best for major releases where rollback is critical.
- Cloud-Native Systems: Works well with AWS, Azure, or Kubernetes.
- Avoid When: Resource constraints or simple applications don’t justify the cost of dual environments.
Conclusion
Blue-Green Deployment is a powerful strategy for achieving reliable, zero-downtime deployments in SRE. By maintaining two identical environments, it minimizes risk and ensures seamless updates, making it ideal for mission-critical systems. As organizations increasingly adopt cloud-native and microservices architectures, Blue-Green Deployment will remain a cornerstone of SRE practices.
Future Trends
- Integration with AI: AI-driven monitoring could predict Green environment failures before traffic switches.
- Serverless Blue-Green: Serverless platforms like AWS Lambda may adapt Blue-Green strategies.
- GitOps Adoption: Tools like ArgoCD will further automate Blue-Green workflows.
Next Steps
- Explore tools like Spinnaker or Harness for advanced deployment orchestration.
- Experiment with Blue-Green in a sandbox environment using AWS Free Tier or Minikube.
- Join SRE communities like the SREcon conference or Reddit’s r/sre for insights.
Resources
- Official AWS Blue-Green Deployment Guide
- Martin Fowler’s Blog on Blue-Green Deployment
- Continuous Delivery Book