Introduction & Overview
What is Ansible?
Ansible is an open-source automation tool designed for IT tasks such as configuration management, application deployment, and orchestration. Developed by Michael DeHaan in 2012 and acquired by Red Hat in 2015, Ansible is known for its simplicity, agentless architecture, and use of human-readable YAML files for defining automation tasks. It enables Site Reliability Engineers (SREs) to automate repetitive tasks, ensure system consistency, and improve operational efficiency across diverse infrastructure environments.
History or Background
- Origin: Created by Michael DeHaan, also known for Cobbler and Func, to simplify IT automation.
- Acquisition: Red Hat acquired Ansible in 2015, integrating it into their enterprise offerings.
- Evolution: Ansible has grown from a command-line tool to include enterprise solutions like Red Hat Ansible Automation Platform, with community-driven contributions via Ansible Galaxy.
- Community: Backed by a robust open-source community, Ansible has extensive documentation and thousands of reusable roles and modules.
Why is Ansible Relevant in Site Reliability Engineering?
Ansible aligns with SRE principles by automating infrastructure management, reducing toil, and ensuring reliability at scale. Its relevance includes:
- Automation of Toil: Automates repetitive tasks like server configuration, patching, and compliance checks, freeing SREs for higher-value work.
- Scalability: Manages thousands of nodes, from on-premises servers to cloud instances, ensuring consistent configurations.
- Reliability: Enforces idempotency, ensuring predictable system states even after repeated operations.
- Collaboration: Simplifies cross-team workflows by using readable YAML playbooks, bridging development and operations.
Core Concepts & Terminology
Key Terms and Definitions
- Control Node: The machine where Ansible is installed and commands are executed (e.g.,
ansible-playbook). - Managed Node: Remote systems (servers, network devices) managed by Ansible via SSH or WinRM.
- Inventory: A file (INI or YAML) listing managed nodes, grouped by roles (e.g., webservers, dbservers).
- Playbook: A YAML file defining a set of tasks to be executed on managed nodes.
- Module: Reusable scripts (e.g.,
ansible.builtin.aptfor package management) that perform specific tasks. - Role: A structured way to organize tasks, variables, and templates for reusability.
- Ansible Vault: A feature for encrypting sensitive data in playbooks or variables.
- Idempotency: Ensures repeated playbook runs do not alter a system if it’s already in the desired state.
| Term | Definition | Example |
|---|---|---|
| Playbook | YAML file describing automation steps | Install Nginx, configure SSL |
| Task | A single automation step in a playbook | “Install Apache package” |
| Module | Reusable unit of automation | ansible.builtin.copy, ansible.builtin.yum |
| Inventory | List of target servers/hosts | hosts.ini file with IPs |
| Role | Structured way of organizing playbooks | Webserver role, Database role |
| Facts | System information collected by Ansible | OS type, IP, CPU details |
| Handler | Triggered task based on change | Restart service after config update |
| Idempotency | Ensures repeated runs don’t cause unintended changes | Running “install nginx” twice won’t reinstall |
How Ansible Fits into the Site Reliability Engineering Lifecycle
Ansible supports key SRE activities:
- Incident Response: Automates recovery tasks, such as restarting services or restoring configurations.
- Capacity Planning: Provisions infrastructure consistently across environments.
- Monitoring and Observability: Configures monitoring tools and log aggregators.
- Post-Mortem Analysis: Automates compliance checks to prevent recurring issues.
- Change Management: Ensures consistent deployments and rollbacks via playbooks.
Architecture & How It Works
Components and Internal Workflow
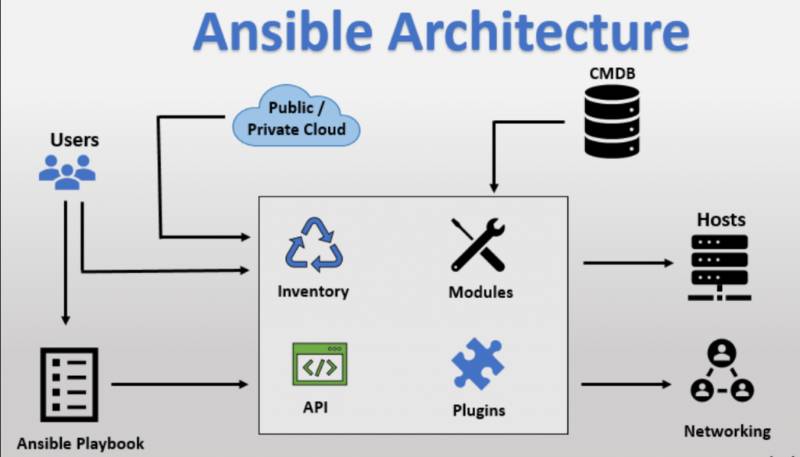
Ansible operates on a push-based, agentless architecture:
- Control Node: Runs Ansible and connects to managed nodes via SSH (Linux) or WinRM (Windows).
- Inventory: Defines managed nodes and groups, stored statically (e.g.,
/etc/ansible/hosts) or dynamically (e.g., from AWS/GCP APIs). - Modules: Small programs pushed to managed nodes, executed, and removed after completion.
- Playbooks: YAML files orchestrate tasks, calling modules with specified parameters.
- Plugins: Extend functionality (e.g., connection plugins for SSH, callback plugins for logging).
Workflow:
- The control node reads the inventory and playbook.
- Ansible connects to managed nodes, copies modules, and executes tasks.
- Results are returned in JSON format, ensuring idempotency and error handling.
Architecture Diagram
Below is a textual representation of Ansible’s architecture (image generation not possible):
[User]
|
v
[Control Node]
| Ansible CLI, Playbooks, Inventory, Ansible.cfg
| Python + SSH/WinRM
v
[Managed Nodes]
| Linux (SSH, Python) | Windows (WinRM, PowerShell)
| Modules executed temporarily
v
[Cloud/External Systems]
| AWS, Azure, GCP, Kubernetes (via dynamic inventory)
- User: Initiates automation via playbooks or ad-hoc commands.
- Control Node: Central hub running Ansible, managing connections.
- Managed Nodes: Target systems receiving configurations.
- Cloud/External Systems: Integrated via dynamic inventory or APIs.
Integration Points with CI/CD or Cloud Tools
- CI/CD: Integrates with Jenkins, GitLab CI, or GitHub Actions to automate deployments. Example: Ansible playbooks triggered post-build to configure servers.
- Cloud: Supports AWS, Azure, GCP via modules (e.g.,
amazon.aws.ec2_instance) for provisioning and configuration. - Containerization: Manages Kubernetes/OpenShift clusters using
kubernetes.corecollections. - Version Control: Playbooks stored in Git for versioning and collaboration.
Installation & Getting Started
Basic Setup or Prerequisites
- Control Node: Linux/Unix (e.g., Ubuntu, CentOS) or Windows with WSL, Python 3.5+, pip.
- Managed Nodes: Python 2.4+ (Linux) or PowerShell 3.0+ (Windows), SSH/WinRM access.
- Network: OpenSSH for Linux, WinRM for Windows, network access to managed nodes.
- Optional: Ansible Galaxy for roles, Ansible Vault for secrets.
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
- Install Ansible (Ubuntu):
sudo apt update
sudo apt install software-properties-common
sudo apt-add-repository --yes --update ppa:ansible/ansible
sudo apt install ansible2. Verify Installation:
ansible --version3. Create Inventory File (inventory.yml):
all:
hosts:
web1:
ansible_host: 192.168.1.10
ansible_user: admin
children:
webservers:
hosts:
web1:4. Test Connectivity:
ansible -i inventory.yml all -m pingOutput:
web1 | SUCCESS => {
"changed": false,
"ping": "pong"
}5. Write a Simple Playbook (webserver.yml):
---
- name: Configure web server
hosts: webservers
become: yes
tasks:
- name: Install Apache
ansible.builtin.apt:
name: apache2
state: latest
- name: Start Apache
ansible.builtin.service:
name: apache2
state: started
enabled: yes6. Run the Playbook:
ansible-playbook -i inventory.yml webserver.ymlReal-World Use Cases
Scenario 1: Automating Web Server Configuration
- Context: An SRE team manages 100 web servers across AWS and on-premises.
- Task: Deploy Apache, configure virtual hosts, and ensure consistent SSL settings.
- Solution: Use an Ansible playbook to install Apache, copy configuration files, and enable services.
- name: Deploy web servers
hosts: webservers
become: yes
tasks:
- name: Install Apache
ansible.builtin.apt:
name: apache2
state: latest
- name: Copy SSL config
ansible.builtin.copy:
src: ssl.conf
dest: /etc/apache2/conf-available/ssl.conf
- name: Enable Apache service
ansible.builtin.service:
name: apache2
state: started
enabled: yesScenario 2: Disaster Recovery Automation
- Context: A financial institution needs rapid recovery of services post-outage.
- Task: Restore configurations and restart services on affected servers.
- Solution: Ansible playbooks automate service restoration and configuration checks, minimizing downtime.
- name: Restore database service
hosts: dbservers
become: yes
tasks:
- name: Ensure MySQL is running
ansible.builtin.service:
name: mysql
state: started
- name: Restore config
ansible.builtin.copy:
src: my.cnf
dest: /etc/mysql/my.cnf
backup: yesScenario 3: Compliance and Security Policy Enforcement
- Context: A healthcare provider must enforce HIPAA-compliant security policies.
- Task: Apply user permissions, patch systems, and configure firewalls.
- Solution: Ansible automates policy enforcement across all servers.
- name: Enforce security policies
hosts: all
become: yes
tasks:
- name: Ensure only approved users
ansible.builtin.user:
name: "{{ item }}"
state: present
loop:
- admin
- sre
- name: Apply security patches
ansible.builtin.apt:
upgrade: dist
update_cache: yesScenario 4: CI/CD Pipeline Integration
- Context: A tech startup uses Jenkins for CI/CD and Ansible for deployments.
- Task: Automate application deployment to Kubernetes.
- Solution: Ansible integrates with Jenkins to deploy applications using
kubernetes.coremodules.
- name: Deploy app to Kubernetes
hosts: localhost
tasks:
- name: Apply Kubernetes deployment
kubernetes.core.k8s:
state: present
definition: "{{ lookup('file', 'app-deployment.yaml') }}"Benefits & Limitations
Key Advantages
- Simplicity: YAML-based playbooks are easy to read and write.
- Agentless: No software installation required on managed nodes.
- Scalability: Manages thousands of nodes efficiently.
- Community Support: Extensive modules and roles via Ansible Galaxy.
- Idempotency: Ensures consistent system states.
Common Challenges or Limitations
- Performance: Slower for very large deployments compared to agent-based tools like Puppet.
- Learning Curve: Advanced features (e.g., dynamic inventories) require familiarity with Python and YAML.
- Error Handling: Debugging complex playbooks can be challenging without tools like
ansible-lint. - Windows Support: Less mature than Linux support, requiring PowerShell and WinRM.
Best Practices & Recommendations
Security Tips
- Use Ansible Vault to encrypt sensitive data:
ansible-vault encrypt secrets.yml - Restrict SSH access with specific users and keys.
- Use least-privilege accounts for Ansible tasks.
Performance
- Use
--forksto parallelize tasks:ansible-playbook --forks 50 playbook.yml. - Cache facts to reduce execution time:
ansible.builtin.setup: cache=True. - Validate playbooks with
ansible-lintbefore execution.
Maintenance
- Organize playbooks into roles for reusability.
- Store playbooks in Git for version control.
- Regularly update Ansible and modules:
pip install --upgrade ansible.
Compliance Alignment
- Define security policies as playbooks to enforce compliance.
- Use
ansible.builtin.auditmodule to log changes for audits.
Automation Ideas
- Automate log rotation and monitoring setup.
- Integrate with monitoring tools like Prometheus for automated alert configurations.
- Use dynamic inventories for cloud environments.
Comparison with Alternatives
| Feature | Ansible | Puppet | Chef | SaltStack |
|---|---|---|---|---|
| Architecture | Agentless (SSH/WinRM) | Agent-based | Agent-based | Agent-based or agentless |
| Configuration Language | YAML (Playbooks) | Puppet DSL | Ruby DSL | YAML |
| Ease of Use | High (simple syntax) | Moderate (steeper learning curve) | Moderate (Ruby knowledge needed) | High (similar to Ansible) |
| Scalability | Excellent (thousands of nodes) | Excellent (enterprise-grade) | Excellent | Excellent (event-driven) |
| Windows Support | Good (via WinRM) | Strong | Strong | Moderate |
| Community | Large (Ansible Galaxy) | Large | Large | Growing |
| Best For | Simple automation, cloud integration | Complex enterprise environments | Customizable workflows | Real-time automation |
When to Choose Ansible
- Choose Ansible: For agentless setups, cloud integrations, or when simplicity and quick setup are priorities.
- Choose Alternatives: Puppet/Chef for complex enterprise environments; SaltStack for event-driven automation.
Conclusion
Final Thoughts
Ansible is a powerful, flexible tool for SREs, enabling automation of infrastructure management, compliance, and deployments. Its agentless architecture and YAML-based playbooks make it accessible, while its scalability supports enterprise needs. Future trends include deeper integration with AI-driven automation (e.g., Red Hat Ansible Automation Platform) and event-driven workflows.
Next Steps
- Explore advanced topics like Ansible Tower/AWX for enterprise management.
- Contribute to the Ansible community via GitHub or Ansible Galaxy.
- Experiment with dynamic inventories for cloud environments.