1. Introduction & Overview
What is Scalability?
Scalability refers to a system’s ability to handle an increasing amount of work or its potential to be enlarged to accommodate growth. In DevSecOps, scalability ensures that development, security, and operations processes can grow without sacrificing performance, reliability, or security.
History or Background
- Traditional IT environments often lacked dynamic scalability, requiring manual scaling or overprovisioning.
- The shift to DevOps emphasized automation and elasticity.
- The evolution to DevSecOps introduced the need for scalable security practices, ensuring that security controls scale in tandem with infrastructure and code.
Why is it Relevant in DevSecOps?
- Ensures security measures scale with infrastructure and workloads.
- Critical for CI/CD pipelines, which need to run multiple builds, tests, and deployments simultaneously.
- Supports cloud-native architectures like microservices and containers, which demand elastic security policies.
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Horizontal Scaling | Adding more nodes or instances to distribute the load. |
| Vertical Scaling | Adding more power (CPU, RAM) to an existing node. |
| Elasticity | The system’s ability to automatically adjust capacity. |
| Load Balancer | Distributes incoming traffic across multiple servers. |
| Auto-scaling | Automatic addition or removal of compute resources based on metrics. |
| Immutable Infrastructure | Deploying updates by replacing rather than modifying infrastructure. |
How It Fits into the DevSecOps Lifecycle
| DevSecOps Phase | Scalability Relevance |
|---|---|
| Plan | Anticipate future growth and load. |
| Develop | Design modular, scalable codebases. |
| Build | Parallel builds and dynamic resource allocation. |
| Test | Scale automated security tests across microservices. |
| Release | Handle multiple concurrent releases with resilience. |
| Deploy | Auto-scale deployment environments. |
| Operate | Scale logging, monitoring, and alerts. |
| Monitor | Real-time scalable observability platforms. |
| Respond | Scalable incident response and threat intelligence. |
3. Architecture & How It Works
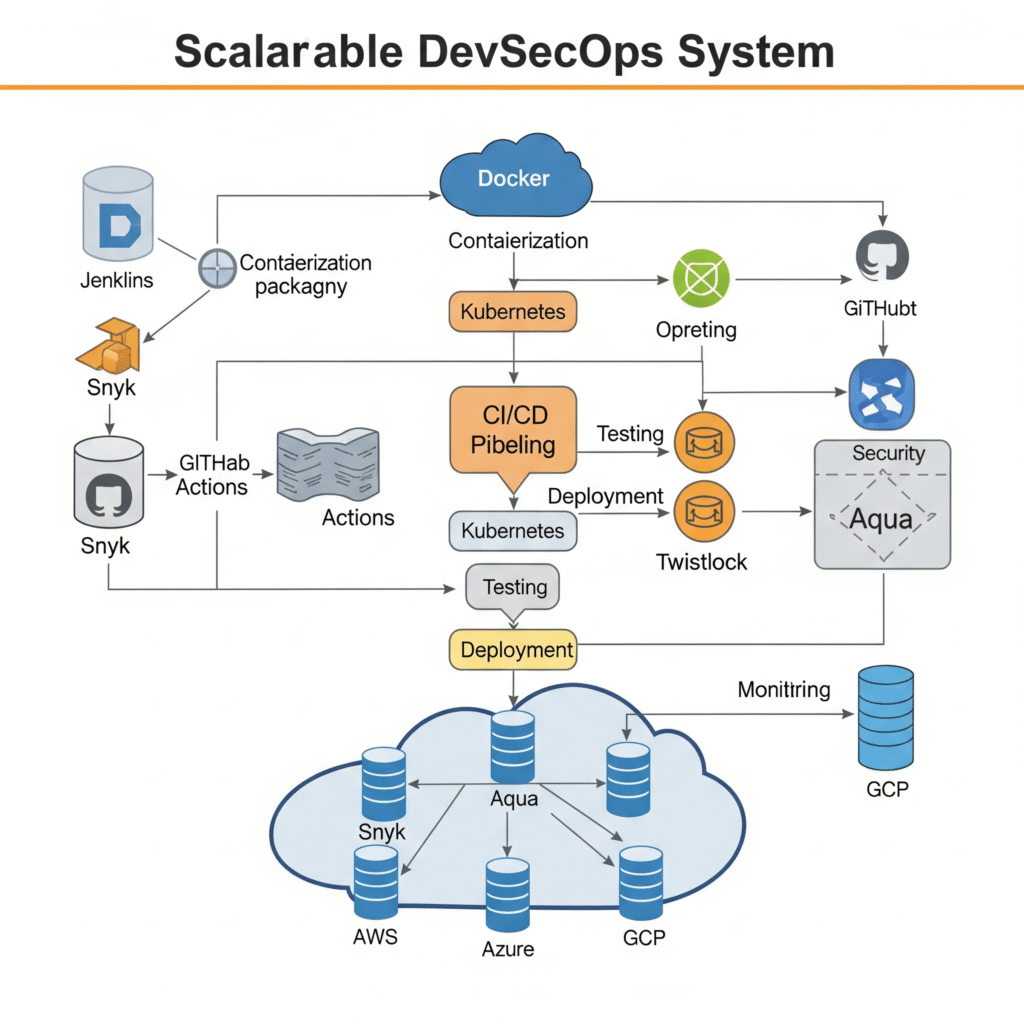
Components of a Scalable DevSecOps System
- Containerization (e.g., Docker)
- Lightweight, fast to scale.
- Orchestration (e.g., Kubernetes)
- Automates scaling, load balancing, and service discovery.
- CI/CD Pipelines (e.g., Jenkins, GitHub Actions)
- Support parallel execution, scalable runners.
- Security Tools (e.g., Snyk, Aqua, Twistlock)
- Integrate dynamically with CI/CD and respond to changes at scale.
- Cloud Infrastructure (e.g., AWS, Azure, GCP)
- Provide native auto-scaling and policy enforcement.
Internal Workflow (Simplified)
[Code Commit]
|
v
[CI/CD Pipeline Triggers] ---> [Auto-scaling Build Agents]
|
v
[Security Scanning Tools] ---> [Dynamic Resource Allocation]
|
v
[Deploy to Orchestrated Env (e.g., Kubernetes)]
|
v
[Runtime Monitoring + Alerts (e.g., Falco, Prometheus)]
Architecture Diagram (Descriptive)
+---------------------+
| Developers |
+---------------------+
|
v
+----------------------------+
| CI/CD Orchestrator | (Jenkins, GitLab CI)
+----------------------------+
| |
v v
+------------+ +----------------+
| Build Nodes| | Security Scans |
+------------+ +----------------+
| |
v v
+-------------------------------+
| Container Orchestration | (Kubernetes Cluster)
+-------------------------------+
| |
v v
+----------------+ +--------------------+
| App Services | | Monitoring Tools |
+----------------+ +--------------------+
Integration Points
| Tool | Integration |
|---|---|
| GitHub Actions | Scale runners using self-hosted GitHub runners on Kubernetes. |
| Jenkins | Jenkins agents auto-scale in cloud-native environments. |
| AWS Auto Scaling Groups | Dynamically manage EC2 instances. |
| Kubernetes HPA | Horizontal Pod Autoscaler adjusts pod replicas. |
| Prometheus + Alertmanager | Alert thresholds trigger scaling events. |
4. Installation & Getting Started
Prerequisites
- Container runtime (Docker)
- Orchestrator (e.g., Minikube or Kubernetes cluster)
- CI/CD platform (e.g., Jenkins or GitHub Actions)
- Cloud account (optional but helpful for advanced auto-scaling)
Step-by-Step Setup Guide (Using Kubernetes)
1. Set up Kubernetes (Minikube for local)
minikube start --cpus=4 --memory=8192
2. Deploy a Scalable Application
# deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: sample-app
spec:
replicas: 2
selector:
matchLabels:
app: sample-app
template:
metadata:
labels:
app: sample-app
spec:
containers:
- name: sample-app
image: nginx
ports:
- containerPort: 80
kubectl apply -f deployment.yaml
3. Enable Horizontal Pod Autoscaler
kubectl autoscale deployment sample-app --cpu-percent=50 --min=2 --max=10
4. Monitor with Metrics Server
kubectl top pods
5. Real-World Use Cases
1. Security Scanning at Scale
- Auto-scale vulnerability scanning tools across multiple microservices using cloud-native runners.
2. Parallel Testing in CI
- Jenkins agents spawn dynamically for each test suite, ensuring tests run concurrently for faster feedback.
3. Scalable Secret Management
- Use HashiCorp Vault auto-scaling with Kubernetes for secret injection into hundreds of pods.
4. Threat Detection in High-Traffic Environments
- Falco or Sysdig deploys scalable detection policies in real-time across multiple workloads.
Industry-Specific Example: FinTech
- High transaction volumes during market hours demand scalable backend and real-time fraud detection systems integrated into CI/CD.
6. Benefits & Limitations
Key Advantages
- Improved Performance: Meet growing demand without bottlenecks.
- Resilience: Avoid downtime by balancing load.
- Efficiency: Dynamic resource provisioning reduces cost.
- Security at Scale: Apply policies uniformly across thousands of instances.
Limitations
- Complexity: Requires mature architecture and monitoring.
- Latency Risks: Misconfigured scaling can cause cold starts or lags.
- Security Drift: Auto-scaling must maintain security baselines.
7. Best Practices & Recommendations
Security Tips
- Enforce IAM least privilege across auto-scaled resources.
- Use infrastructure as code (IaC) to track scalable configurations.
Performance & Maintenance
- Set thresholds and limits for auto-scaling to avoid resource exhaustion.
- Use monitoring tools (e.g., Grafana, Prometheus) for metrics-driven scaling.
Compliance & Automation
- Implement compliance-as-code to ensure scaling actions don’t breach security.
- Automate scaling audits and logging via tools like CloudTrail or Open Policy Agent (OPA).
8. Comparison with Alternatives
| Feature | Scalability | Manual Provisioning | Static Infrastructure |
|---|---|---|---|
| Elastic | ✅ | ❌ | ❌ |
| Efficient | ✅ | ❌ | ❌ |
| Secure (with config) | ✅ | ✅ | ✅ |
| Complex Setup | ⚠️ | ✅ | ✅ |
When to Use Scalability
- When expecting dynamic workloads, multi-tenant systems, or DevSecOps across multiple teams.
- Avoid for monolithic, infrequently updated, or fixed-resource applications.
9. Conclusion
Scalability is not just a DevOps concern—it’s a foundational pillar of DevSecOps. As organizations adopt microservices, containers, and cloud-native infrastructure, scalability ensures that security and operations practices can keep pace with rapid change.
Future Trends
- AI-driven autoscaling
- Policy-aware scaling decisions
- Scalable SBOM (Software Bill of Materials) scanning