1. Introduction & Overview
What is Terraform?
Terraform is an open-source Infrastructure as Code (IaC) tool developed by HashiCorp that allows users to define and provision data center infrastructure using a declarative configuration language called HashiCorp Configuration Language (HCL). Terraform manages infrastructure across a variety of service providers such as AWS, Azure, GCP, Kubernetes, and more.

History or Background
- Launched: 2014 by HashiCorp
- Written in: Go
- Current stable version (as of 2025): v1.8+
- Initially designed to support cloud-native infrastructure automation
- Evolved into a critical component of modern DevOps and DevSecOps workflows
Why is it Relevant in DevSecOps?
- Enables security as code through reusable, version-controlled infrastructure modules.
- Facilitates compliance automation by codifying secure configurations.
- Simplifies auditability with immutable logs and infrastructure states.
- Integrates seamlessly with CI/CD pipelines to enforce secure provisioning.
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| HCL | HashiCorp Configuration Language; used for writing Terraform configurations |
| Plan | Preview of changes Terraform will make to the infrastructure |
| Apply | Execution of planned infrastructure changes |
| State File | JSON file that tracks resources managed by Terraform |
| Module | Reusable, composable group of Terraform resources |
| Provider | Plugin that enables Terraform to interact with APIs of different platforms (e.g., AWS, Azure) |
| Backend | Determines where Terraform state is stored (local, S3, etc.) |
How It Fits into the DevSecOps Lifecycle
Terraform supports multiple DevSecOps stages:
- Plan: Define security-compliant infrastructure as code
- Build: Integrate into CI/CD for automated and repeatable deployments
- Test: Use static code analysis and policy-as-code tools (e.g., Sentinel, OPA)
- Release & Deploy: Secure provisioning with minimal human interaction
- Operate & Monitor: Enable drift detection and consistent audit trails
3. Architecture & How It Works
Components
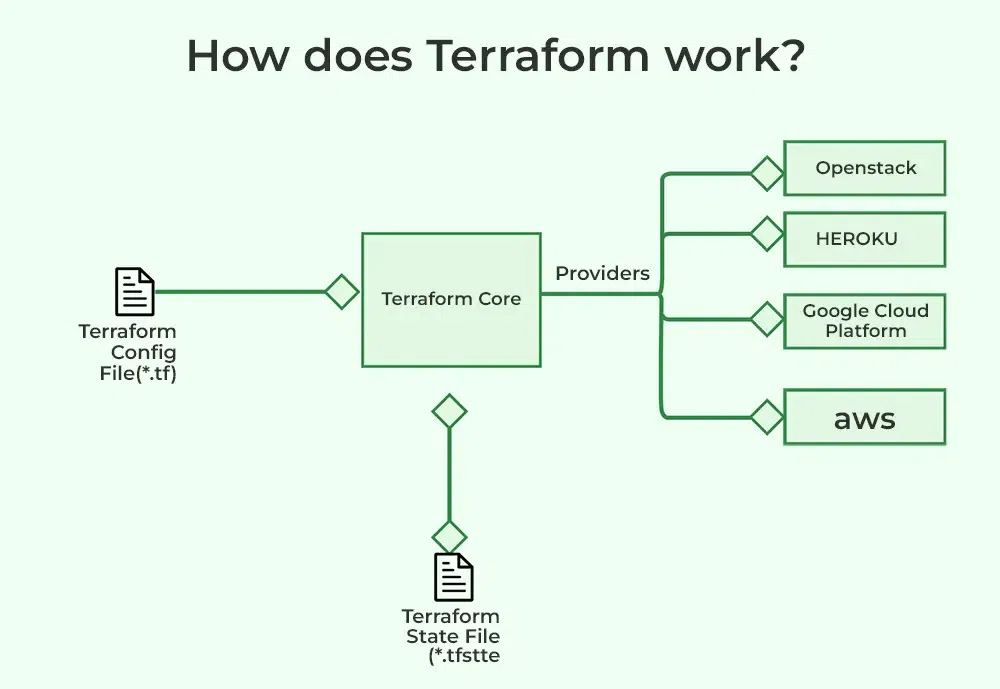
- Terraform CLI: Command-line interface for running Terraform commands
- Terraform Core: Processes configurations, generates execution plans
- Providers: Plugins for cloud or SaaS platforms (e.g.,
aws,azurerm) - State Backend: Stores state for collaboration and history (e.g., remote S3)
- Modules: Abstraction units for infrastructure components (e.g., VPC, Kubernetes cluster)
Internal Workflow
- Write Configuration:
provider "aws" { region = "us-east-1" } resource "aws_s3_bucket" "secure_bucket" { bucket = "my-devsecops-bucket" acl = "private" } - Initialize Terraform:
terraform init - Generate Execution Plan:
terraform plan - Apply Configuration:
terraform apply - Manage State and Changes:
- State file updates
- Drift detection
- Destroy with
terraform destroywhen needed
Architecture Diagram (Textual)
+----------------+ +-------------+ +--------------+
| .tf Files +-----> | Terraform |-----> | Cloud API |
| (HCL Configs) | | Engine | | (AWS, Azure) |
+----------------+ +-------------+ +--------------+
| | |
|---- Modules -------->| |
|---- Variables ------>| |
|<--- State File ------| |
Integration Points with CI/CD or Cloud Tools
- CI/CD: GitHub Actions, GitLab CI, Jenkins, CircleCI
- Security Scanning: tfsec, Checkov, Bridgecrew
- Compliance: Sentinel (HashiCorp), OPA
- Cloud Integration: AWS IAM, Azure RBAC, Google IAM
4. Installation & Getting Started
Basic Setup or Prerequisites
- Install Terraform CLI: https://www.terraform.io/downloads
- Cloud provider credentials (e.g., AWS access key/secret key)
- Git for version control
- Optional: Docker, tfenv (version manager), IDE with Terraform plugins
Step-by-Step Beginner-Friendly Guide
Step 1: Install Terraform
brew install terraform # macOS
choco install terraform # Windows
Step 2: Create a Directory and Configuration File
mkdir devsecops-terraform && cd devsecops-terraform
touch main.tf
Step 3: Write a Simple AWS Resource
provider "aws" {
region = "us-west-2"
}
resource "aws_s3_bucket" "secure_bucket" {
bucket = "my-devsecops-bucket"
acl = "private"
}
Step 4: Run Terraform Commands
terraform init # Initializes project
terraform plan # Previews changes
terraform apply # Provisions resources
5. Real-World Use Cases
Use Case 1: Secure Multi-Cloud Infrastructure Provisioning
- Use Terraform to manage and secure infrastructure across AWS, Azure, and GCP.
- Apply consistent security policies using modules.
Use Case 2: Security Hardened Kubernetes Clusters
- Deploy EKS with restricted IAM roles, encrypted storage, and network policies.
- Use third-party modules (e.g.,
terraform-aws-modules/eks/aws) to enforce best practices.
Use Case 3: Automated DevSecOps Pipelines
- Integrate Terraform with GitLab CI for zero-touch, policy-checked deployments.
- Scan Terraform code with Checkov or tfsec before each deployment.
Use Case 4: Disaster Recovery and Backup Automation
- Provision and version immutable backup buckets with encryption and logging.
- Implement failover routing with Route53, all codified in Terraform.
6. Benefits & Limitations
Key Advantages
- Idempotency: Ensures consistent infrastructure state
- Version Control: Git-managed infrastructure code
- Multi-cloud Support: Unified tool for diverse environments
- Compliance Automation: Declarative compliance checks
- Modular Design: Reusable and composable infrastructure blocks
Limitations
| Limitation | Description |
|---|---|
| State Management Complexity | Requires careful backend configuration |
| Learning Curve | HCL and IaC require time to master |
| Debugging Difficulties | Errors can be abstract or low-level |
| Sensitive Data in State Files | Must use encryption and secret management tools |
| Limited Procedural Logic | Not suited for complex imperative logic |
7. Best Practices & Recommendations
Security Tips
- Enable encryption on state files (e.g., AWS S3 + KMS)
- Use
terraform validate,tflint,tfsecfor secure code - Minimize use of hardcoded secrets; integrate with secret managers (e.g., AWS Secrets Manager)
Performance & Maintenance
- Use
terraform planbefore everyapply - Archive old state versions using Terraform Cloud or remote backends
- Modularize code for reusability and separation of concerns
Compliance & Automation
- Implement Sentinel or OPA policies to enforce security/compliance
- Automate plan + apply via CI/CD pipelines with approval gates
- Monitor drift and audit changes regularly
8. Comparison with Alternatives
| Tool | Language | Cloud Support | Strengths | Weaknesses |
|---|---|---|---|---|
| Terraform | HCL | Multi-cloud | Broad community, modular, declarative | Manual state mgmt |
| Pulumi | Python/TS | Multi-cloud | Familiar languages, dynamic | Smaller community |
| AWS CloudFormation | YAML/JSON | AWS only | Deep AWS integration | AWS-centric |
| Ansible | YAML | Agentless | Procedural logic, good for config | Less ideal for IaC |
When to Choose Terraform
- When working in multi-cloud environments
- When you need modular, reusable, and scalable infrastructure code
- When integrating with CI/CD pipelines and security policies
9. Conclusion
Terraform stands out as a foundational tool in the DevSecOps ecosystem. Its declarative nature, extensive cloud provider support, and seamless CI/CD integration make it ideal for secure, scalable infrastructure automation.
Future Trends
- Policy as Code (PaC): More adoption of tools like Sentinel, OPA
- Drift Detection & Self-Healing: Enhancements in automated correction
- State Security Improvements: Encrypted and fine-grained state access
Next Steps
- Dive deeper into Terraform modules and backends
- Explore integrations with Sentinel, tfsec, or Bridgecrew
- Join the community and contribute to open-source modules.